6 Free Tools To Help You Run Windows Applications On Linux
When switching from Windows to a more secured Linux operating system, you may come up with many difficulties. Like for example you might not find the applications you needed for doing your daily work. Although you can find any and all the replacements of a Windows application on Linux, there is a way through which you can run your favorite Windows application on your Linux operating system. Here we have compiled a list of 6 free tools that will help you run your favorite Windows application on a Linux system or help you to run virtual PC on any Operating System.
You are welcome to share if you know more free tools that will help you run your favorite Windows application on a Linux
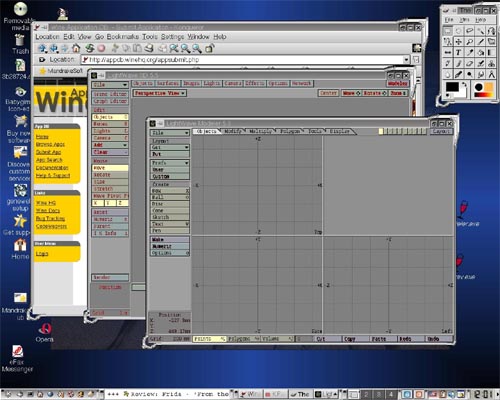
Wine is an Open Source implementation of the Windows API on top of X, OpenGL, and Unix. Think of Wine as a compatibility layer for running Windows programs. Wine does not require Microsoft Windows, as it is a completely free alternative implementation of the Windows API consisting of 100% non-Microsoft code, however Wine can optionally use native Windows DLLs if they are available. Wine provides both a development toolkit for porting Windows source code to Unix as well as a program loader, allowing many unmodified Windows programs to run on x86-based Unixes, including Linux, FreeBSD, Mac OS X, and Solaris.
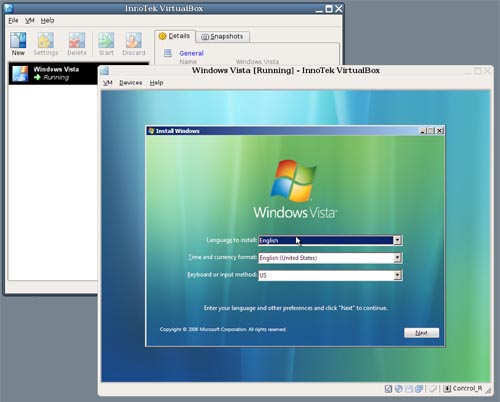
VirtualBox is an x86 virtualization software package, originally created by German software company innotek, now developed by Sun Microsystems as part of its Sun xVM virtualization platform. It is installed on an existing host operating system; within this application, additional operating systems, each known as a Guest OS, can be loaded and run, each with its own virtual environment. Supported host operating systems include Linux, Mac OS X, OS/2 Warp, Windows XP or Vista, and Solaris, while supported guest operating systems include FreeBSD, Linux, OpenBSD, OS/2 Warp, Windows and Solaris.
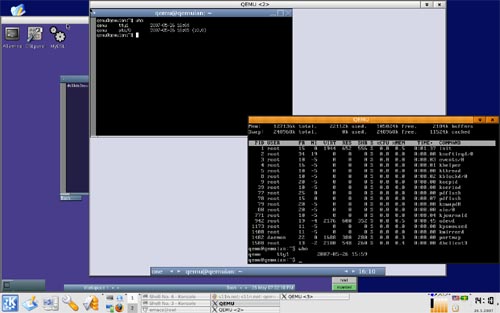
QEMU is a generic and open source machine emulator and virtualizer. When used as a machine emulator, QEMU can run OSes and programs made for one machine (e.g. an ARM board) on a different machine (e.g. your own PC). By using dynamic translation, it achieves very good performances. When used as a virtualizer, QEMU achieves near native performances by executing the guest code directly on the host CPU. A host driver called the QEMU accelerator (also known as KQEMU) is needed in this case. The virtualizer mode requires that both the host and guest machine use x86 compatible processors.
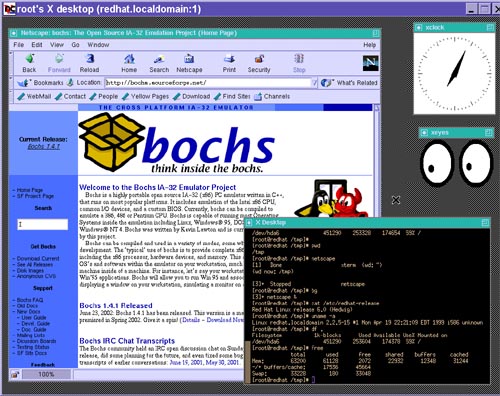
Bochs is a highly portable open source IA-32 (x86) PC emulator written in C++, that runs on most popular platforms. It includes emulation of the Intel x86 CPU, common I/O devices, and a custom BIOS. Currently, Bochs can be compiled to emulate a 386, 486, Pentium/PentiumII/PentiumIII/Pentium4 or x86-64 CPU including optional MMX, SSEx and 3DNow! instructions. Bochs is capable of running most Operating Systems inside the emulation including Linux, DOS, Windows® 95/98 and Windows® NT/2000/XP or Windows Vista. Bochs was written by Kevin Lawton and is currently maintained by this project.
rdesktop is an open source client for Windows Terminal Services, capable of natively speaking Remote Desktop Protocol (RDP) in order to present the user’s Windows desktop. Supported servers include Windows 2000 Server, Windows Server 2003, Windows Server 2008, Windows XP, Windows Vista and Windows NT Server 4.0. Rdesktop currently runs on most UNIX based platforms with the X Window System, and other ports should be fairly straightforward.
The Xen® hypervisor, the powerful open source industry standard for virtualization, offers a powerful, efficient, and secure feature set for virtualization of x86, x86_64, IA64, PowerPC, and other CPU architectures. It supports a wide range of guest operating systems including Windows®, Linux®, Solaris®, and various versions of the BSD operating systems. The Xen hypervisor is a unique open source technology, developed collaboratively by the Xen community and engineers at over 20 of the most innovative data center solution vendors, including AMD, Cisco, Dell, HP, IBM, Intel, Mellanox, Network Appliance, Novell, Red Hat, SGI, Sun, Unisys, Veritas, Voltaire, and Citrix. Xen is licensed under the GNU General Public License (GPL2) and is available at no charge in both source and object format. Xen is, and always will be, open sourced, uniting the industry and the Xen ecosystem to speed the adoption of virtualization in the enterprise.