In order to shutdown or restart the Windows with just one click shortcut or from command line, users can use shutdown command line utility/command that comes with Windows 2000 (with the Resource Kit installed) and Windows XP or Windows Vista (native). To access shutdown command, simply go to DOS command prompt by clicking on Start -> All Programs -> Accessories -> Command Prompt or Start -> Run and then type in Cmd to launch a command prompt window.
Type shutdown -s -t 01 Here "01" Means time for shutdown in no. of Seconds.
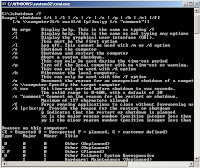
If you want brief discription for shutdown command
Type shutdown /? in command line
Type shutdown -s -t 01 Here "01" Means time for shutdown in no. of Seconds.
If you want brief discription for shutdown command
Type shutdown /? in command line

