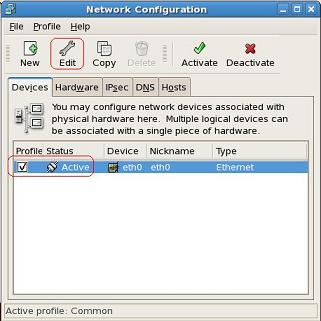
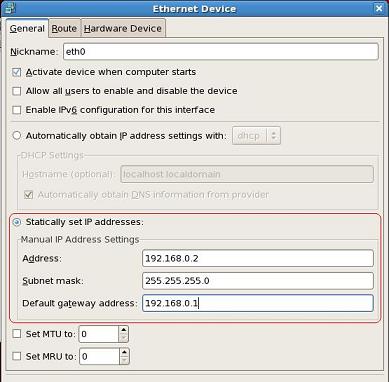
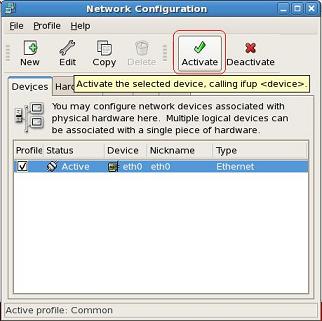
HP Data Protector software
Introduction
HP Data Protector software simplifies application protection in virtual and physical environments through unified recovery and advanced automation. Global, one-touch backup configuration and a wide range of disk-based recovery options across HP and non-HP arrays, including fully-automated application recovery, help you meet any SLA for up to 70% less total cost of ownership than competitive backup software solutions.
More than 41,000 customers around the world, and nearly half of the Global 500, rely on HP Data Protector software to protect their critical applications and data. Data Protector is a key component of the HP Information Management solution portfolio, which dramatically simplifies the management and governance of information for today's modern enterprise organization.
What's New
Extending the Power of HP - down-to-the-second recovery of application for HP P4000 arrays.
Only HP Data Protector software can recover virtual server applications and data to any point in time - down-to-the-second - from a centralized console without scripting. Data Protector 6.2 extends this functionality to the P4000. Together, Data Protector and P4000 achieve a highly cost-effective enterprise recovery solution ideal for virtual server deployments of applications such as Microsoft SharePoint, Microsoft Exchange and SQL Server.
Data Protector allows backup administrators to select the point in time to which they'd like to recover into the Data Protector console. Data Protector accesses the application transaction log (where all of the application's transactions are recorded before they're processes and/or written to data files) and fills in the data gaps between snapshots. Data Protector then synchronizes the application with the data and restarts the application. This functionality is possible with any Data Protector recovery solution whether from snapshot, disk or tape.
Extending simplified snapshot functionality to non-HP arrays such as EMC CLARiiON and Network Appliance
Data Protector Zero Downtime Backup snapshot support has been extended to non-HP arrays through VSS integration. Global one-touch protection ensures snapshot configurations - as well as all backup methods - are automatically extended to new virtual machines, Microsoft databases, and Oracle databases as they're brought online. One click in the Data Protector console and Data Protector will automatically apply the chosen backup method to new VMs and databases. This level of automation extends to physical environments as well.
Reducing the burden of single item recovery on the backup administrator.
Data Protector Granular Recovery Extension empowers SharePoint and VMware vSphere administrators to recover single items directly from the application administrator's console, without asking for assistance from the backup administrator.
Data Protector allows application administrators to recover single items from Data Protector disk or tape backups - they don't need to know or use Data Protector, nor do they need to contact the backup administrator. For SharePoint environments, GRE allows application administrators to recover single items from ANY 3rd party snapshots.
NEW Data Protector Reporter software - sophisticated operational analysis, SLA compliance reporting across multi-site distributed geographies.
Data Protector software includes robust reporting capabilities, including a notification function which allows customers to forward events to HP or 3rd-party reporting or management tools such as HP Storage Essentials and IBM Tivoli. For customers who require the most advanced reporting capabilities, HP provides Data Protector Reporter software - which delivers enterprise reporting, designed specifically for Data Protector customers. HP Data Protector Reporter software is customer-installable software which delivers centralized, automated reporting to optimize operations and infrastructure - and realize up to 30% savings. It features a powerful reporting engine that drives global, multi-site backup and restore analysis. Data Protector Reporter features 35+ out-of-the-box reports including SLA and performance reporting. The optional current licensed module provides enhanced powerful customized ad-hoc query and analysis flexible reporting. For more information, please download the Data Protector Reporter QuickSpecs on hp.com/go/dataprotector.
Enhanced single-pass disaster recovery functionality - for no additional cost.
Data Protector 6.2 introduces new disaster recovery functionality which is included in the cost of Data Protector. Unlike some backup software solutions that require you to keep a separate image backup from which to initiate recovery, Data Protector provides "single-pass DR" - which enables customers to create a disaster recovery image from any existing full backup. You can restore from physical-to-virtual and virtual-to-physical servers across dissimilar hardware. In addition, once the backup administrator initiates the disaster recovery process, Data Protector automatically re-builds the system and the partitioning. Data Protector 6.2 supports both Linux and Windows operating systems - for specific support please check the compatibility matrix on hp.com/go/dataprotector.
In addition, Data Protector DR functionality is especially useful in remote and branch office environments. Data Protector is fully replication aware, and provides a single management console from which to oversee deduplication-enabled replication between local or geographically distributed sites. When Data Protector performs a backup in the remote office, the backup with the DR image can be replicated to the central data center, In the event of an outage, the DR image can be prepared and delivered to the ROBO site via FTP site or by shipping a USB drive for fast recovery.
IPv6 and NDMP
Data Protector 6.2 is fully IPv6 compliant. Data Protector IPv6 support is backward compatible for IPv4 environments. In addition, Data Protector 6.2 also provides NDMP snapmirror to tape support, which provides efficient backup of large files.
Hardware Support and Software Pre-Requisites
| ||||||||||||||||||||||||||||||||||